

{{text-cta}}
Last Friday a security breach involving git repositories was reported. Hackers broke into private repos across GitHub, GitLab, and Bitbucket, wiped them, and asking the project owners for a ransom to be paid within 10 days, or else.
The report mentioned at least 392 repos have been ransomed. The project owners who reported their code had disappeared found the following ransom note in its place:
“To recover your lost code and avoid leaking it: Send us 0.1 Bitcoin (BTC) to our Bitcoin address ES14c7qLb5CYhLMUekctxLgc1FV2Ti9DA and contact us by Email at admin@gitsbackup.com with your Git login and a Proof of Payment.
If you are unsure if we have your data, contact us and we will send you a proof. Your code is downloaded and backed up on our servers.
If we don’t receive your payment in the next 10 Days, we will make your code public or use them otherwise.”
Why it happened and how it could have been avoided
The hacker supposedly combed through the Internet for git config files, then extracted credentials listed in plain text to gain access. The compromised accounts have account passwords stored in plaintext deployed to related repositories.
A couple of recommended best practices the project owners could have followed:
1. Don’t commit personal config files into source control.
Because committing those personal config files is unnecessary, could be counterproductive, and might have security implications if you expose details about your machine’s setup.
2. Use a password management tool locked down with two-factor authentication.
How to check your repos for personal git config files
There are two parts to this:
1. Do I have any personal config files anywhere in my repos?
2. How do I make sure I and my fellow teammates won’t commit these files by accident in the future?
Do I have any personal config files in my repos?
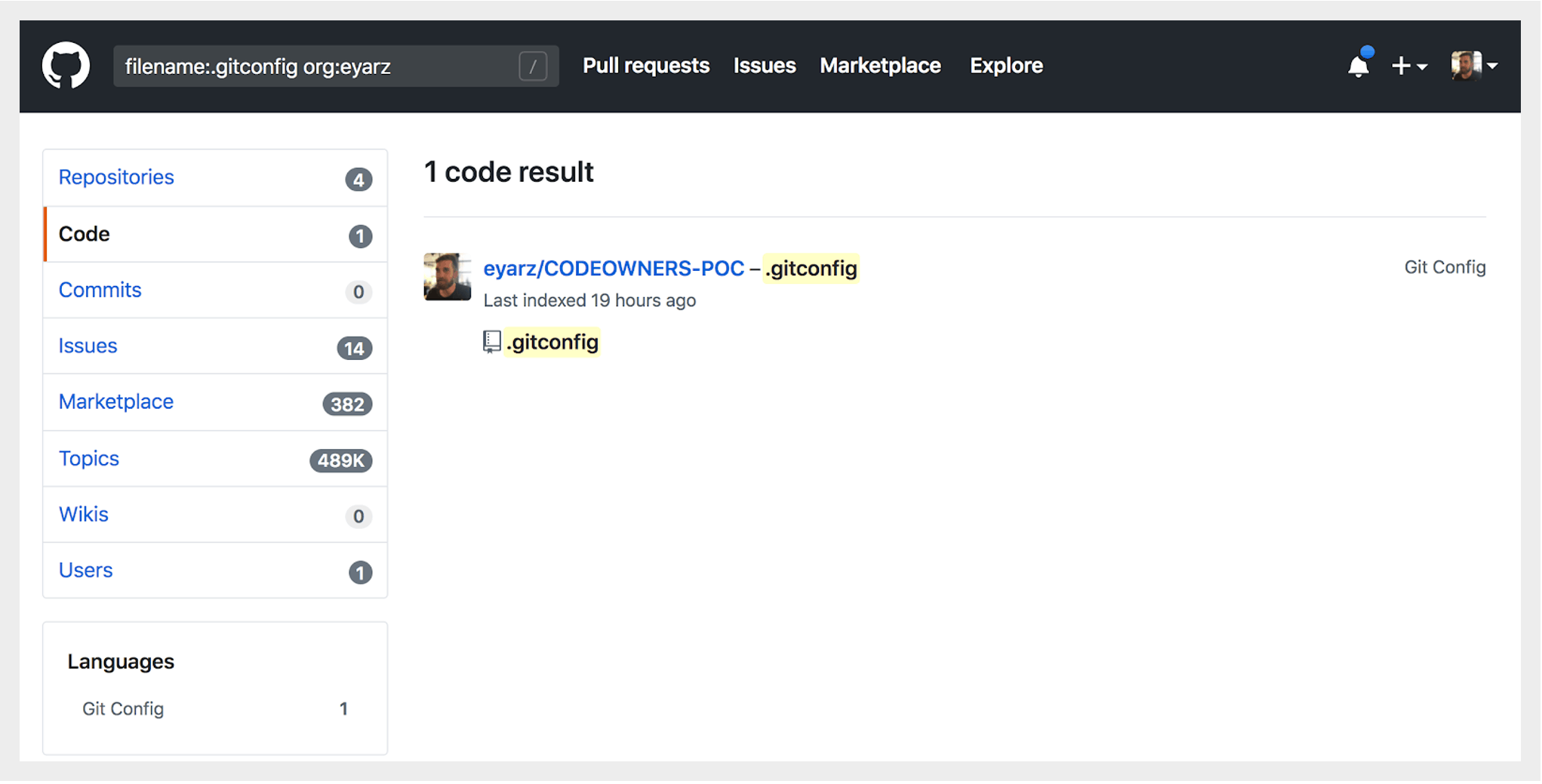
One way to do this would be to use GitHub’s search option to search for “.gitconfig” file type, like so: https://github.com/search?q=filename%3A.gitconfig+org%3Aeyarz (replace “eyarz” with your GitHub account name)
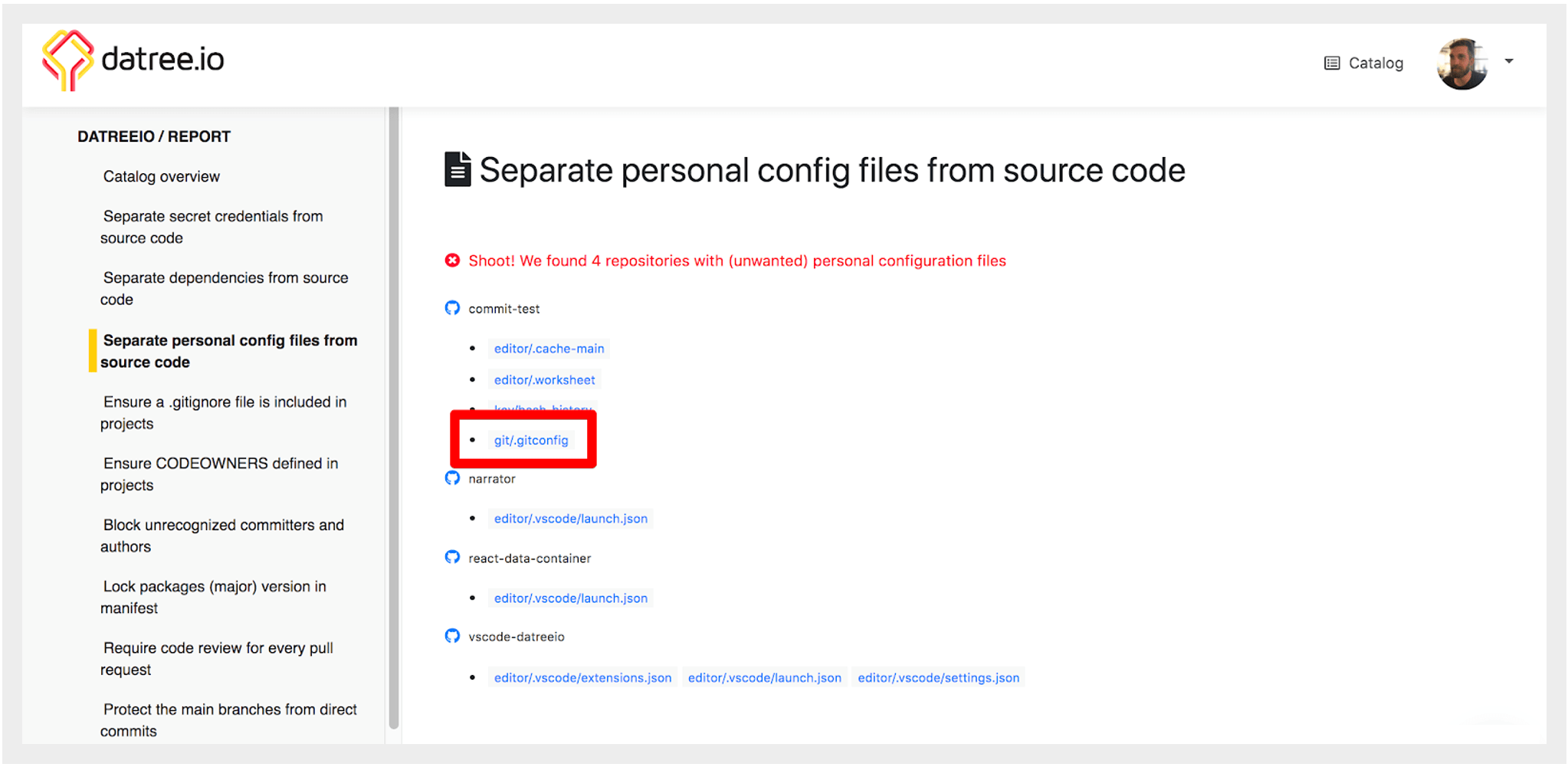
Another way would be to install Datree and use the Status Report feature:
{{text-cta}}
How do I make sure I and my fellow teammates won’t commit these files by accident in the future?
Well, this is harder manually. You can send an email to everyone to remind them about this best practice, or even mandate it as a policy to comply with. But developers who write the code or those doing code reviews will need to remember to check every new pull request for accidental inclusion of personal git config files.
Frankly Datree is the right tool to do this automatically. We have a built-in policy called separate personal config files from source code you can activate on your repos. Once this policy is active, Datree will automatically check each pull request for any personal git config files, and if such files are found, it will either block the PR or warn the committer depending on your preference. Additionally, the policy is active for future new repositories, so it’s a completely “set-and-forget” thing.
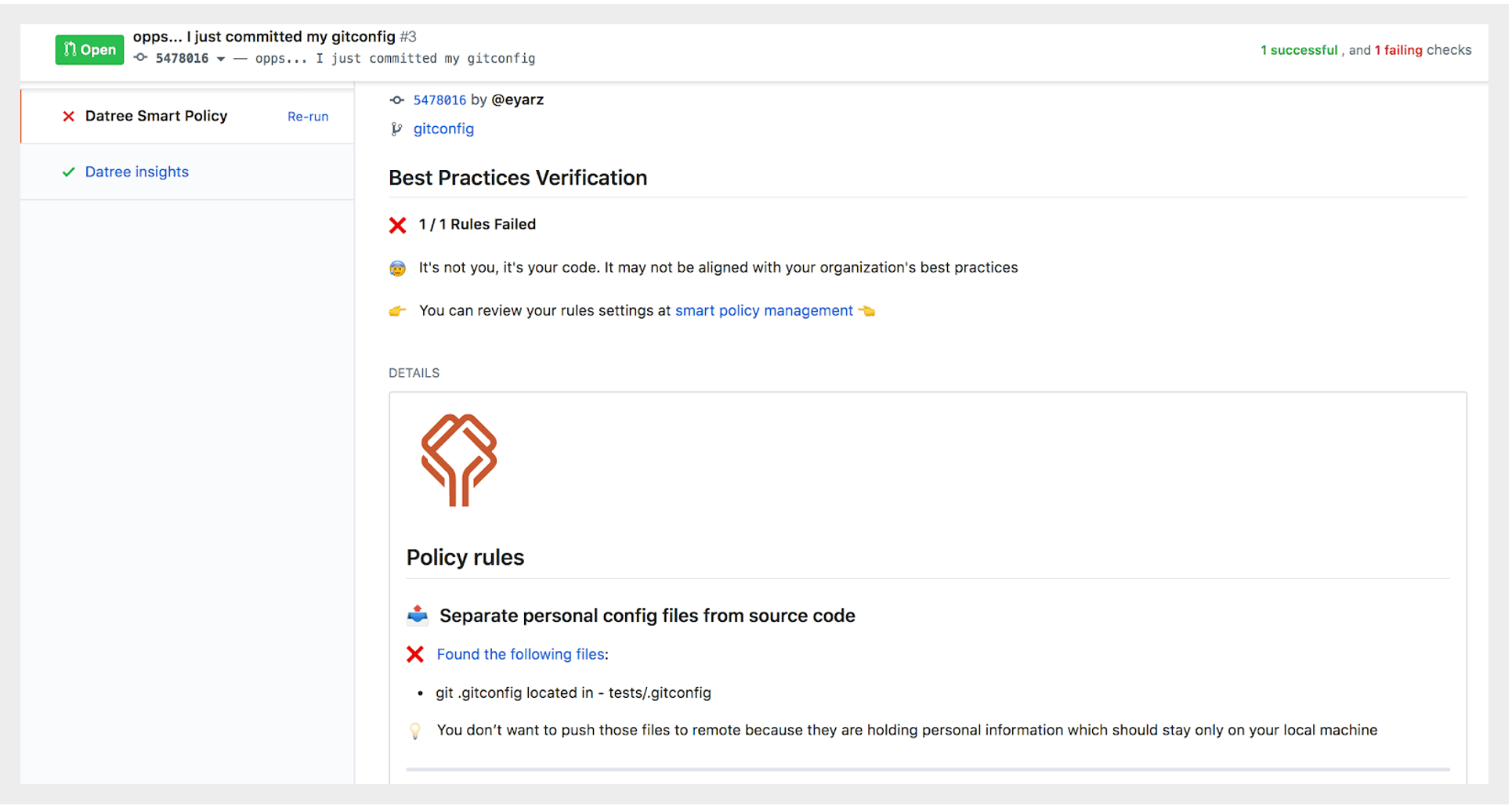
It’s that easy 👍
Learn from Nana, AWS Hero & CNCF Ambassador, how to enforce K8s best practices with Datree
Headingajsdajk jkahskjafhkasj khfsakjhf
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.








%20(1).webp)
.png)
.png)





